IPSec tunnels
I currently manage two LAN networks, physically separated by multiple kilometers. One of these networks hosts my servers (including this website!), and the other hosts my everyday computer. Whenever I needed to gain access to my server, I used OpenVPN to connect my server across these LAN networks. However, this had a few downsides as the OpenVPN tunnel was quite slow, does not like it if my computer’s network is reconnected and some devices don’t have simple OpenVPN implementations.
However, it is also possible to create site-2-site vpn tunnels, where the routers will handle the VPN connection. The following diagram shows an overview of the setup.
Setting up IPSec on two Mikrotik devices is fairly simple, and only requires both to have a public endpoint that is accessible by each device. Setting up an IPSec connection requires the following items to be created in the Miktotik devices:
- Profile
- Identity
- Peer
- Policy
- Proposal
- NAT rule
There are plenty of tutorials online that do a better job of explaining how to set it up, I primarily used this video
My configurations looked as follows
[admin@Mikrotik hAP2] > ip ipsec
[admin@Mikrotik hAP2] /ip ipsec> profile export
# apr/09/2025 22:19:59 by RouterOS 6.48.6
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048 enc-algorithm=aes-256 hash-algorithm=sha512
[admin@Mikrotik hAP2] /ip ipsec> identity export
# apr/09/2025 22:20:03 by RouterOS 6.48.6
/ip ipsec identity
add peer=[removed] secret="[removed]"
[admin@Mikrotik hAP2] /ip ipsec> peer export
# apr/09/2025 22:20:10 by RouterOS 6.48.6
/ip ipsec peer
add address=45.83.4.242/32 exchange-mode=ike2 name=[removed]
[admin@Mikrotik hAP2] /ip ipsec> policy export
# apr/09/2025 22:20:19 by RouterOS 6.48.6
/ip ipsec policy
add dst-address=10.0.0.0/13 peer=[removed] proposal=[removed] src-address=10.8.0.0/13 tunnel=yes
[admin@Mikrotik hAP2] /ip ipsec> proposal export
# apr/09/2025 22:20:22 by RouterOS 6.48.6
/ip ipsec proposal
add auth-algorithms=sha512 enc-algorithms=aes-256-cbc name=[removed] pfs-group=modp2048
[admin@Mikrotik hAP2] /ip ipsec> /ip firewall
[admin@Mikrotik hAP2] /ip firewall> nat export
# apr/09/2025 22:22:26 by RouterOS 6.48.6
/ip firewall nat
add action=accept chain=srcnat dst-address=10.0.0.0/13 src-address=10.8.0.0/13Ofcourse, this configuration is mirrored on the other router, with the peer address changed, and the dst/src addresses flipped.
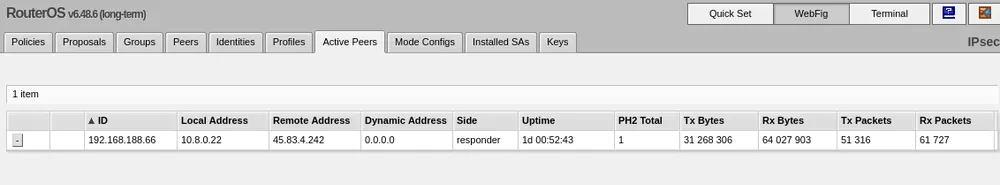
And as you can see, an active peer is created:
And the connection between both networks works perfectly without any configuration on on the individual devices:
user@irondesktop:~ $ ping 10.0.0.1 -c 5
PING 10.0.0.1 (10.0.0.1) 56(84) bytes of data.
From 10.8.0.1: icmp_seq=1 Redirect Host(New nexthop: 10.8.0.22)
64 bytes from 10.0.0.1: icmp_seq=1 ttl=63 time=10.0 ms
64 bytes from 10.0.0.1: icmp_seq=2 ttl=63 time=8.96 ms
64 bytes from 10.0.0.1: icmp_seq=3 ttl=63 time=8.98 ms
64 bytes from 10.0.0.1: icmp_seq=4 ttl=63 time=9.34 ms
64 bytes from 10.0.0.1: icmp_seq=5 ttl=63 time=9.47 ms
--- 10.0.0.1 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4004ms
rtt min/avg/max/mdev = 8.956/9.348/9.999/0.381 msiron@IronServer:~$ traceroute 10.8.0.20
traceroute to 10.8.0.20 (10.8.0.20), 30 hops max, 60 byte packets
1 10.0.0.1 (10.0.0.1) 0.219 ms 0.154 ms 0.102 ms
2 10.8.0.22 (10.8.0.22) 8.981 ms 9.774 ms 9.732 ms
3 10.8.0.20 (10.8.0.20) 10.173 ms 10.560 ms 10.530 ms